Advanced Data Encryption Techniques for Secure Mobile Device Monitoring
Understanding Encryption Basics in Mobile Device Monitoring
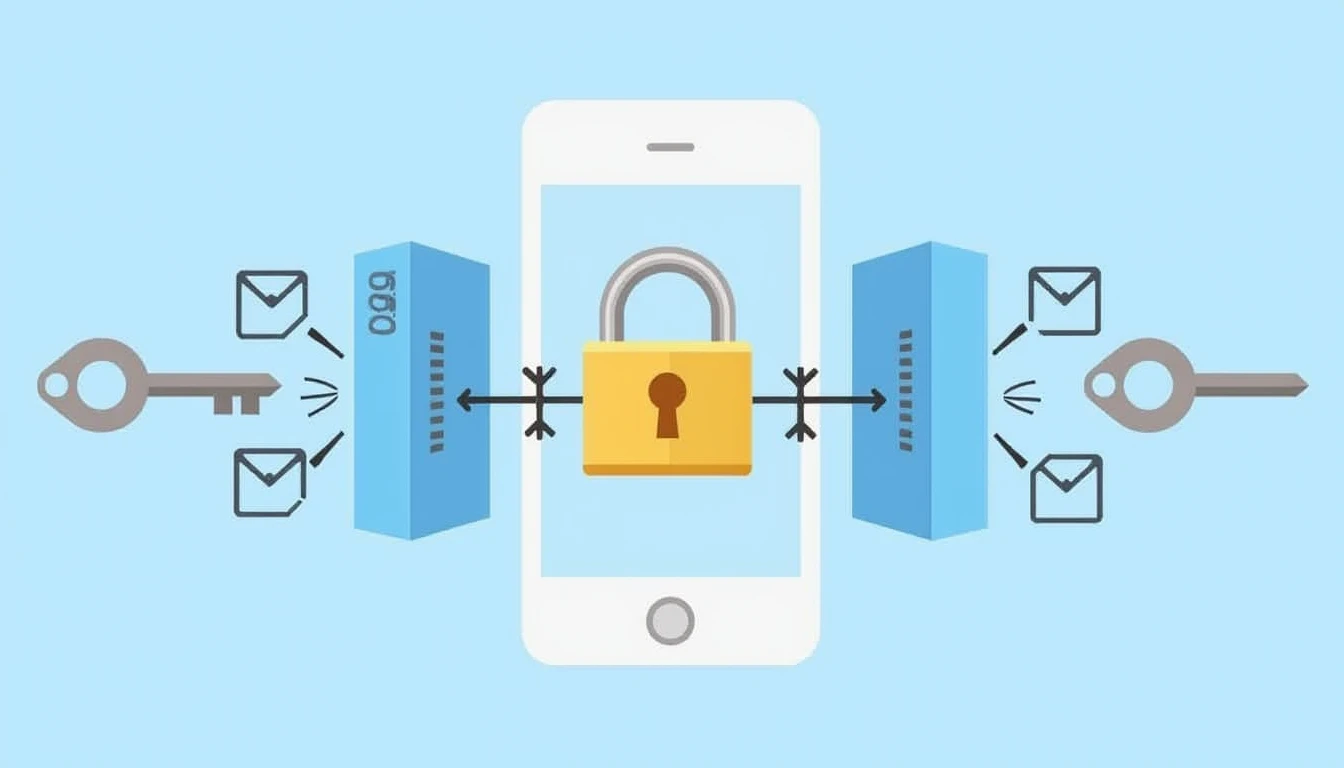
Encryption plays a pivotal role in ensuring that sensitive data remains confidential during monitoring processes. At its core, encryption is the process of converting plain text information into coded language to prevent unauthorized access. This transformation is achieved through complex algorithms that scramble data into an unreadable format, which can only be deciphered by those possessing the correct decryption key.
In the context of smartphone monitoring, encryption serves as a crucial mechanism for securing both transmitted and stored data. When monitoring applications communicate with servers or databases, sensitive information such as location data, usage patterns, and personal communications must be protected from interception. Advanced encryption standards (AES) are commonly employed to encrypt data in transit using robust 256-bit keys, ensuring that even if the communication channels are compromised, the intercepted data remains indecipherable.
Moreover, encryption not only safeguards data during transmission but also while it is stored on servers or local devices. For instance, when monitoring tools collect and store logs of user activities, they often apply encryption techniques to prevent unauthorized access to these records. This ensures that even if a server containing monitored data falls into the wrong hands, the attackers would face significant challenges in extracting usable information due to the strong encryption mechanisms employed.
Implementing End-to-End Encryption for Secure Communication
One of the most effective ways to ensure secure communication during mobile device monitoring is through end-to-end encryption (E2EE). This technique ensures that data remains encrypted throughout its journey from one endpoint (e.g., a user’s smartphone) to another, preventing any intermediary servers or third parties from accessing it.
End-to-end encryption operates by generating unique keys for each communication session. These keys are used to encrypt the data at the sender’s end and can only be decrypted by the intended recipient using their corresponding private key. This process eliminates any potential vulnerabilities that could arise if data were to pass through insecure intermediary points during transmission. In a monitoring context, this means that even if an attacker manages to intercept the encrypted communication between a user’s device and the monitoring server, they would not be able to decrypt or access the data without the private key.
Moreover, implementing E2EE in mobile device monitoring introduces additional layers of security by integrating public-key infrastructure (PKI). This involves generating pairs of cryptographic keys for each monitored device—a public key used for encryption and a private key for decryption. The use of PKI ensures that only authorized devices or users can decrypt the data, significantly reducing the risk of unauthorized access. Additionally, E2EE facilitates secure authentication between monitoring tools and user devices, ensuring that all interactions are authenticated before any data is transmitted.
Secure Key Management in Mobile Device Monitoring
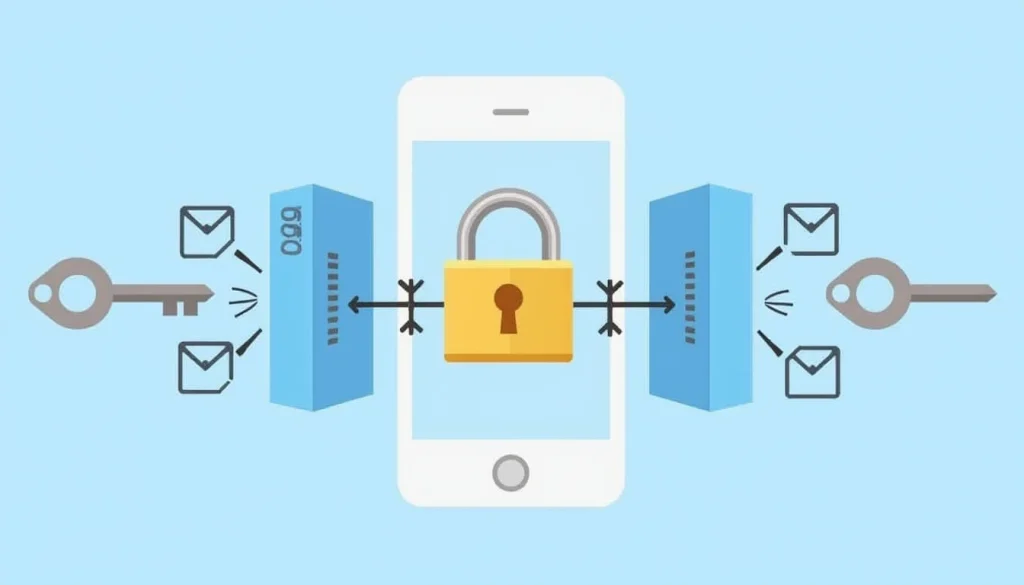
Effective key management is essential for maintaining a robust encryption framework within mobile device monitoring systems. Properly managed keys ensure that encrypted data can be accessed by authorized users while preventing unauthorized access. However, managing these cryptographic keys presents several challenges, especially in large-scale monitoring environments involving numerous devices and users.
Firstly, secure key distribution mechanisms are crucial to prevent the interception of keys during transmission. This often involves using trusted third-party certificate authorities (CAs) or employing advanced key exchange protocols such as Diffie-Hellman or Elliptic Curve Cryptography (ECC). These protocols ensure that both the monitoring server and user devices can securely establish a shared secret without exposing it to potential eavesdroppers. Additionally, key distribution should be managed through secure channels, ensuring that only authorized entities receive the necessary keys.
Furthermore, key storage is another critical aspect of secure key management in mobile device monitoring. Keys need to be stored securely both on local devices and remote servers. For instance, hardware security modules (HSMs) can be used to store cryptographic keys within dedicated hardware that provides additional layers of protection against unauthorized access or tampering. Similarly, encryption-protected databases are often employed for storing keys in cloud environments, ensuring that even if the database is compromised, the keys remain inaccessible without proper decryption mechanisms.
Data Integrity and Authentication through Digital Signatures
Ensuring data integrity and authentication is a vital aspect of secure mobile device monitoring, particularly when dealing with sensitive information. One effective method to achieve this is by utilizing digital signatures, which provide both non-repudiation and tamper-proof guarantees for monitored data.
Digital signatures work by generating a unique hash value from the original data using cryptographic algorithms such as SHA-256 or MD5. This hash value is then encrypted with the sender’s private key to create a signature. The recipient can verify the integrity of the data by recalculating the hash and comparing it against the decrypted signature received from the sender. If both values match, the recipient can be assured that the data has not been altered during transmission.
In mobile device monitoring, digital signatures are particularly useful for validating the authenticity of transmitted logs or reports. For example, when a user’s smartphone sends usage data to a monitoring server, a digital signature can confirm that the data was indeed sent by the authorized device and has not been tampered with en route. This is crucial in industries where regulatory compliance requires verifiable records, such as healthcare or finance.
Additionally, digital signatures provide non-repudiation, ensuring that neither the sender nor receiver can deny their involvement in the communication. This feature is especially valuable for legal purposes when disputes may arise regarding data ownership or authenticity. By incorporating digital signatures into mobile device monitoring systems, organizations can enhance trust and accountability while maintaining robust security measures.
Balancing Security with User Privacy
While encryption techniques provide essential protection for monitored data, it is crucial to strike a balance between security and user privacy. Overly restrictive security policies may lead to user resistance or dissatisfaction, potentially undermining the effectiveness of monitoring initiatives. Therefore, implementing encryption in mobile device monitoring must be done thoughtfully to ensure that both security and privacy are preserved.
One way to achieve this balance is through transparent communication with users regarding how their data will be handled. Providing clear explanations about encryption methods used, data protection measures, and why these precautions are necessary can foster trust between the organization and its users. This transparency not only reassures users but also helps in complying with legal regulations that mandate user consent for monitoring activities.
Moreover, implementing granular controls over monitored data access can further enhance privacy while maintaining security. For instance, organizations can allow users to opt-in or out of certain types of monitoring, such as location tracking or app usage analysis. By offering this level of control, users feel more empowered and less likely to perceive the monitoring activities as intrusive or invasive.
Lastly, leveraging anonymization techniques during data processing can significantly reduce privacy concerns while still enabling valuable insights for monitoring purposes. Anonymizing user data involves removing personally identifiable information (PII) from datasets before analysis, ensuring that individual identities cannot be traced back through the collected data. This approach allows organizations to derive meaningful patterns and trends without compromising users’ personal information, thus achieving a harmonious balance between security and privacy.